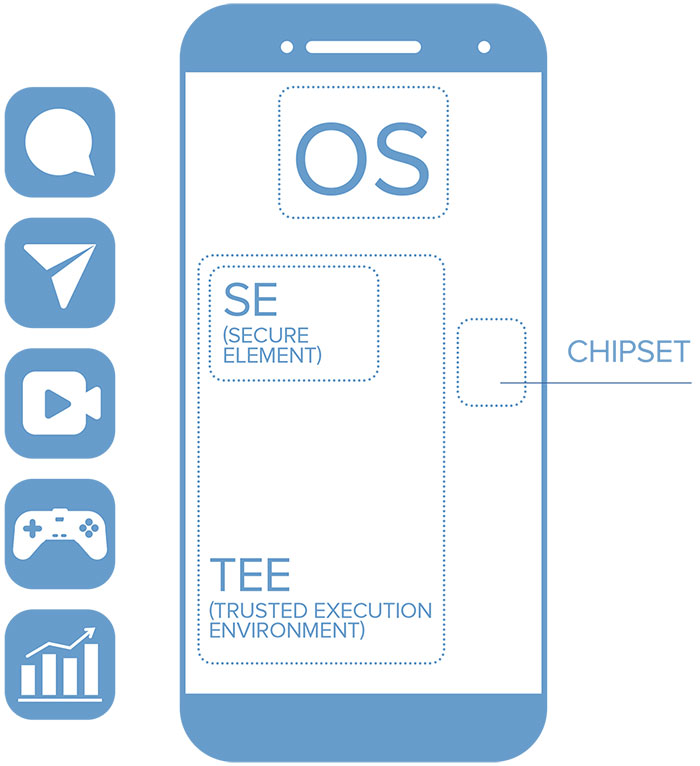
- How to assess the processing performed on your sensitive data by applications or phones?
- How to protect the critical operations of your mobile applications and trustlets (payment, content sharing, games, IoT controller)?
- How to build compliance of your mobile environments (PSD2) and secure interactions with external components?